I am working on an implementation of the
UDP Options draft
at work, this
morning I got the
udp_input
side of processing building. This needs to be
test and gotten working before moving on, before setting up some VMs to test
this I need a way to generate packets with UDP Option data appended.
This seemed like a great occasion to use
go
a little more. There is the
gopacket
library from google that provides raw packet stuff.
images/
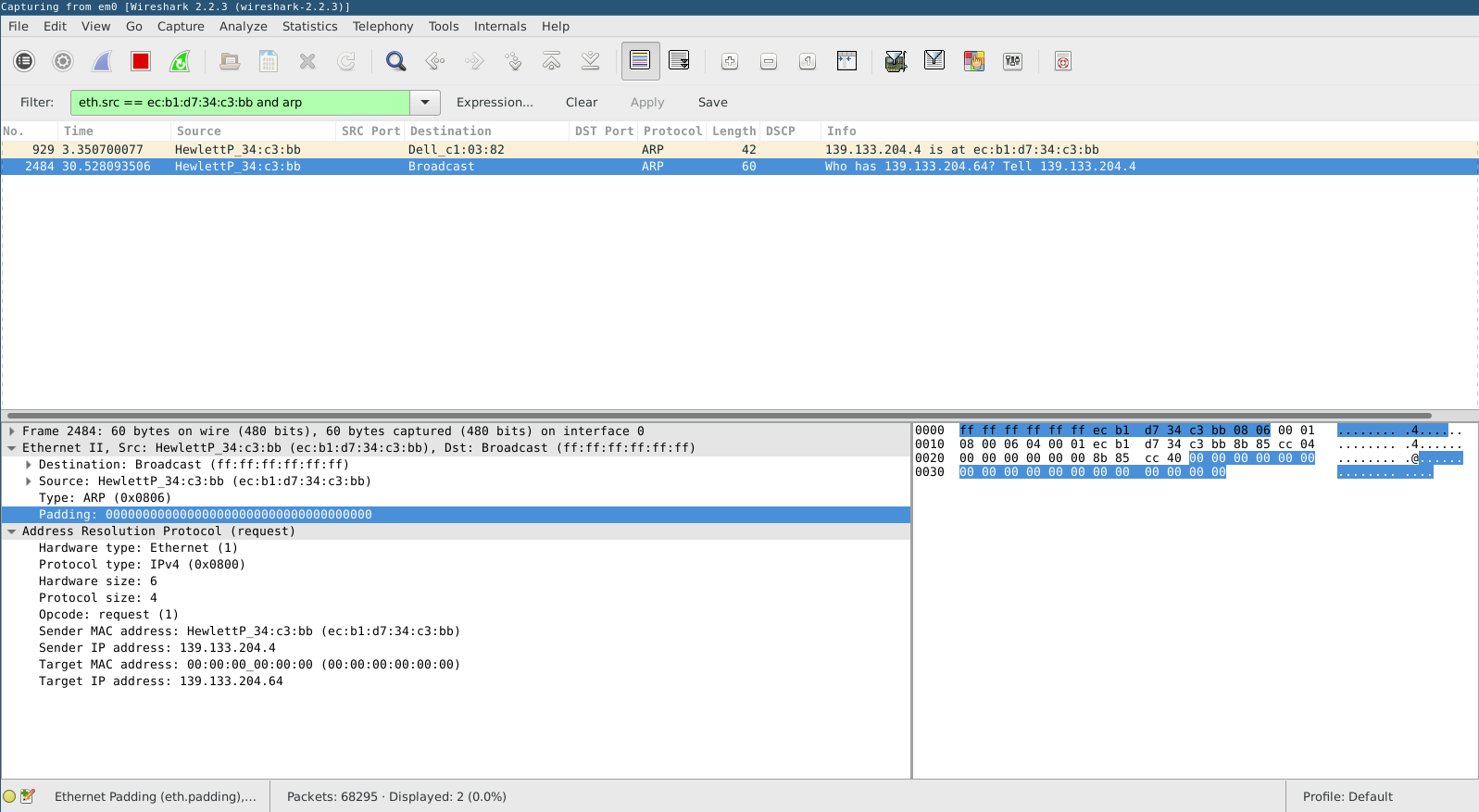
I tried for ages to put together a send example that didn't depend on linux.
Eventually I got to the point where I could form crazy malformed arp packets. I
got to the point of generating the above traces in
wireshark
, for some reason
go was sticking 16 bytes into the address fields and creating madness. You will
note in the above arp packet that the length is much longer, that is because go
is appending some extra data for shits and giggles.
Giving up on go I had a look at the python libraries for generating packets,
they are all about the same level of insanity. The
pathspider
project has
some
test probes
for UDP Options using
scapy
.

pathspider
is a lot of stuff to pull in to generate UDP datagrams, I
extracted out the relevant stuff to use with
scapy
directly:
from scapy.all import IP
from scapy.all import UDP
from scapy.all import *
if __name__ == "__main__":
ip = IP(src="139.133.204.4", dst="139.133.204.64")
udp = UDP(sport=2600, dport=2600)
pkt = ip/udp/"Hello world"
pkt.getlayer(1).len = len(pkt.getlayer(1)) #force UDP len
send((pkt/"\x01\x01\x01\x00"))
You can add the numbers together to find that the extra option space is
include, you can also see the
01 01 01 00
bytes at the end of the packet
which are the options I add.
Reading:
Gun Machine, The Difference Engine
There is this pdf ebook
that I want to read, but it has a really annoying
'DRAFT' water mark on every page. I looked for an automatic way to remove the
watermark and found a
really handly superuser
answer that completely covers
it.
$ pdftk original.pdf output uncompressed.pdf uncompress
$ sed -e "s/watermarktextstring/ /" uncompressed.pdf > unwatermarked.pdf
$ pdftk unwatermarked.pdf output fixed.pdf compress
Before I ran that I tried grepping through the pdf for the string 'DRAFT', now
the pdf was compressed so I didn't find anything. I wanted to make sure the
watermark was just a string so I extract just the first page with
pdfseperate
.
$ pdfseparate -f 1 -l 1 ipv6_for_ipv4_experts_en_a4.pdf out.pdf
I opened
out.pdf
with
inkscape
and played with editing the watermark, which
was indeed just text. I then round tripped the pdf through
pdftk
and
generated a watermark free pdf.
Reading:
Gun Machine, The Difference Engine
With installing my new desktop I am also going to move my 4G modem. I wanted to
get some signal strength numbers so I could be sure I wasn't completely ruining
things for myself. My router has a hand status page that among sensitive
private information has signal strength, SNR and noise numbers.
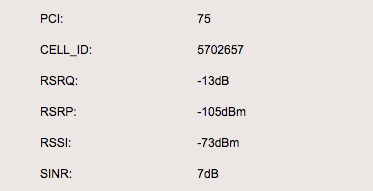
On that page there is also a
CELL_ID
field. The
field is the unique network
id
of the base station you are connected to. This is apparently useful for
location lookups, the wikipedia page has a list of databases that use this
field.
I tried to feed my
CELL_ID
into some of these databases, but they all wanted
more information.
MCC
and
MCN
are pretty easy to find, there is a big table
on the wikipedia page
. I was not able to resolve down a
LAC
from
anywhere. There are apps I could try, but I don't really want to install any of
them on my phone.
Reading:
Gun Machine, The Difference Engine
I am finally starting to make a dent in the pile of things I could be using,
but aren't. A friend gave me a motherboard, case, graphics card and power
supply over about 18 months, in the past fortnight I finally put it all
together and had a working computer.
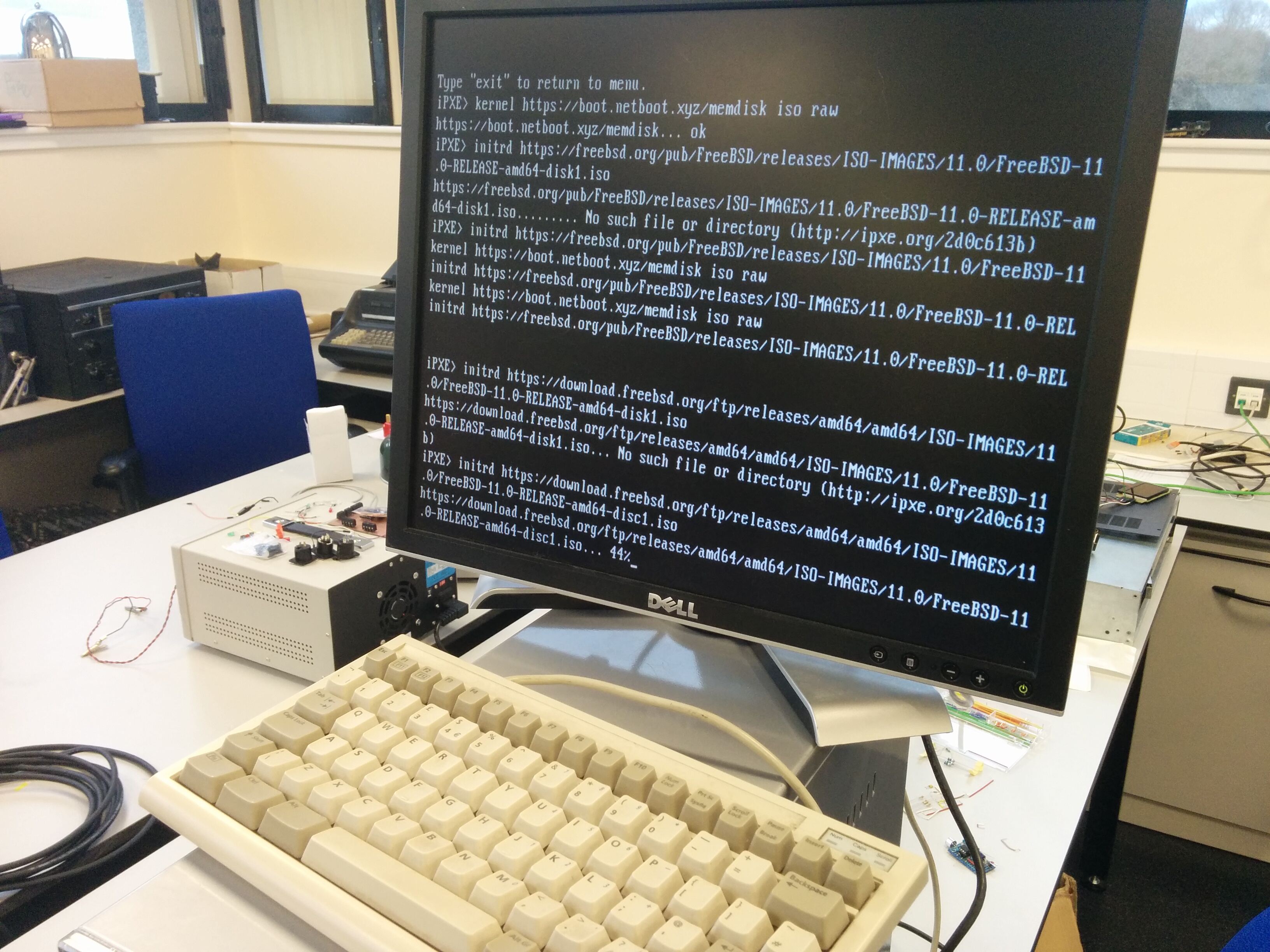
The machine came up no problem, one of the drives I recycled from another
machine and it already had FreeBSD on it. It turns out the motherboard I was
given doesn't want to boot from USB at all.
We tried all the different configurations and eventually fell back to using
PXE. There is an excellent graphic PXE boot environment available from
netboot.xyz
, there was a FreeBSD entry in the OS boot menu, but it this
is not a supported boot method for FreeBSD.
netboot.xyz uses a
mfsboot FreeBSD image
to launch a live system over
PXE. The image is created with a set of
scripts available on github
.
FreeBSD supports booting from a bundled memory image configured with the kernel
config, it looks like that is the feature that makes all of this possible.
It
is
Sunday, so that
makes
seven
days
of
writing
.
Reading:
Gun Machine, The Difference Engine
Not that I can fix any of those either.
I set up
ssl with Let's Encrypt
for
an experiment
yesterday following
a handy
guide on the FreeBSD wiki
. The guide suggested
this mozilla
tool
for generating server configs with good parameters.
With the tool I was only able to hit an A rating on the
ssllabs
testing
site, the A+ rating was annoyingly elusive. I am using
nginx
as vhost for a
go web service, for HSTS a header has to be appended to the response. The
config from Mozilla does this for
nginx
like this:
# HSTS (ngx_http_headers_module is required) (15768000 seconds = 6 months)
add_header Strict-Transport-Security max-age=15768000;
But, the hosted application has control over the response headers.
nginx
can
be configured to always set the header with the
always
flag:
# HSTS (ngx_http_headers_module is required) (15768000 seconds = 6 months)
add_header Strict-Transport-Security "max-age=15768000" always;
Reading:
Gun Machine, The Difference Engine



