
Winter is here, stepping out this morning it was -2, hopefully the start of
some nice seasonal weather with a showering of snow and not the minimum
temperature for the year.
The twitters tell me that
Bunnie Huang
of
Hacking the Xbox
,
Breaking
SD Cards
,
The Essential Guide to Electronics in Shenzhen
and a ton of
other cool things has a
new book in the works
. I read Hacking the Xbox
when it was released for Free after Aaron Swartz's death, the book is an
excellent read and gave me a ton of insights about electronics and breaking
physical things. The new book is in early access, which means you can read it
if you think reading tiny bits of a book is a good idea.
While on the
nostarch
I looked at another early access book,
Attaching
Network Protocols
. The cover, looking a
Tardigrade
at a glance(it
isn't), drew me in, the awesome title didn't hurt.
Hopefully the internet will come alive and tell me when these two books are
finished and available.
Reading:
Reamde
Of course that snowy picture was taken up a mountain, but it was only about 4
degrees up there. Warmer than it seems it is going to get to today.
Last night at the
hacker space
I finally got around to building hardware
out for my emfcamp badge powered
satellite tracker
. Most of the time
was spent hot gluing together foam board to make a stand for the servos I
integrated the control code with the TCP server and the whole thing is
controllable from gpredict now.
When testing servos, knifes are the recommended indicator devices.
Reading:
Reamde

Today I've got nothing. At my desk there are a load of started and unfinished
projects, parts for other things, kits from
boldport club
to be made.
Nothing that is interesting even in its started state, components to make cools
things, coolness sold separately.
At the
hackerspace
tonight I will try to finish my
sat tracker
, but
even that is a fallback project. The projects I want to have completed have
such a high bar to entry.
I wonder if my brain empties out in cycles.
Reading:
Reamde
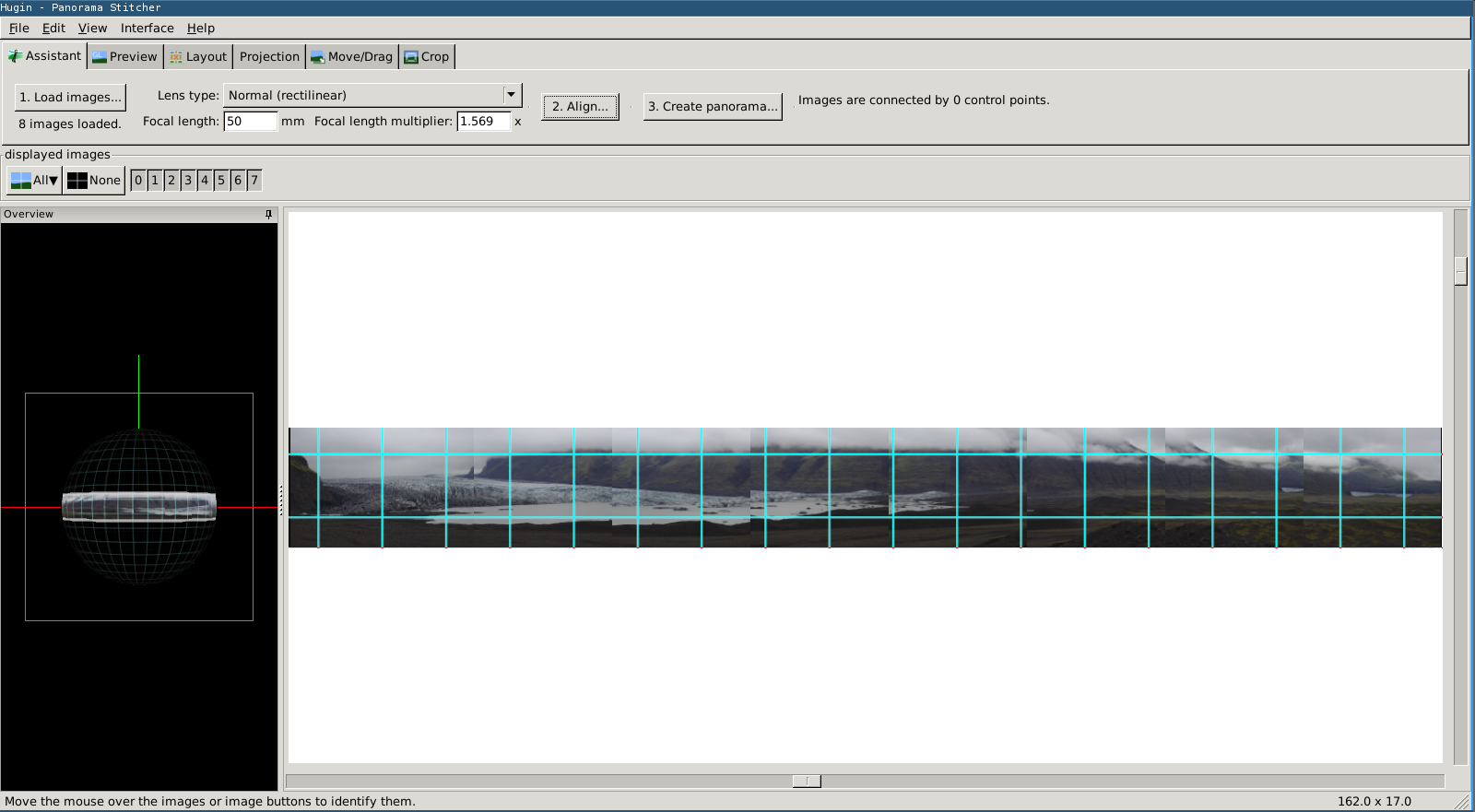
My Idea
to use the
hugin stitching
software to make a panorama from
some images I found on my camera seems to have hit a snag. I am convinced I
didn't have a tripod with me and took the panorama in a haphazard fashion, I
remember the area by the glacier being much much colder than the campsite we
were staying in and I was pushed to leave.
I opened up the 8 images I had to try and stitch together and while they sort
of fall out in a reasonable orde I think it is going to take some time with the
software to get them together. Unless I find the
more magic button
.
Reading:
Reamde



